
Virtual CISOs: The Advantages of Hiring a vCISO
In today’s digital landscape, robust cybersecurity infrastructure is an essential element of any business. The role of the Chief Information Security Officer (CISO) is pivotal
Architecture, implementation, and management of security controls for startups and enterprises.
By combining the Zero Trust Security model with the NIST security frameworks, we identify and eliminate your organization’s blind spots!
Security Operations, Cloud infrastructure, and compliance programs are all part of our complete Zero Trust turnkey service.
We do not rely on checklists to identify threats. We take a holistic approach to identify all your exposures and mitigate all possible attack vectors.
With AI-assisted capabilities, Prodigy 13 combines next-gen security tools with the strongest standards, benchmarks and compliance frameworks.
We guarantee that your organization will see immediate improvements in security posture and defense capabilities!

As part of our managed (or assisted) Zero Trust Cybersecurity service, we cover everything from public cloud providers, on-site infrastructure, application security (SDLC), and compliance.
We provide complete Zero Trust architecture, implementation, management, monitoring, compliance, audit assistance, on-demand consulting, and training services.
We can secure your remote workforce and globally distributed teams.
Investing in your cybersecurity posture is no longer seen as an expense, but rather as an investment in your organization’s future.
By 2025, 60% of organizations will use cybersecurity risk as a primary determinant in conducting third-party transactions and business engagements

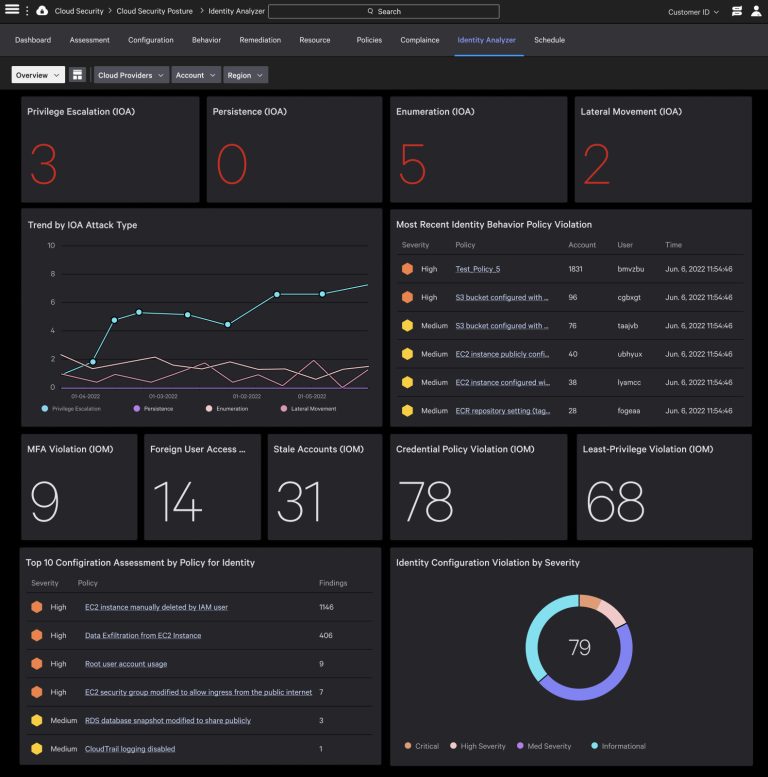
Using the Zero Trust Security model, we ensure 100% coverage with zero blind spots.
Our services adhere to the highest levels of security frameworks, benchmarks, and standards, such as NIST 800-53, FedRAMP, CIS, and MITRE ATT&CK.
We offer affordable fees that are a fraction of the cost of typical Security Engineers or Managed Security Providers (MSP).
Extensive experience with the most popular compliance and auditing frameworks: SOC 2, ISO 27001, PCI DSS, NIST, HIPAA, HITRUST, GDPR, CCPA
To all of our clients, we provide free Penetration Testing, free Vulnerability Management, and Client Questionnaire management.
Our management team has over 80 years of combined experience in the field of information security.







The Zero Trust Security framework was created to respond to the ever-changing threat landscape. For more information please visit our Zero Trust page.
We design our services around the most rigorous and effective standards and security frameworks, including: NIST 800-53 / CSF, Zero Trust, CIS Top 18, CIS Benchmarks, OWASP Top 10, FedRamp, SOC 2, and ISO 27001.
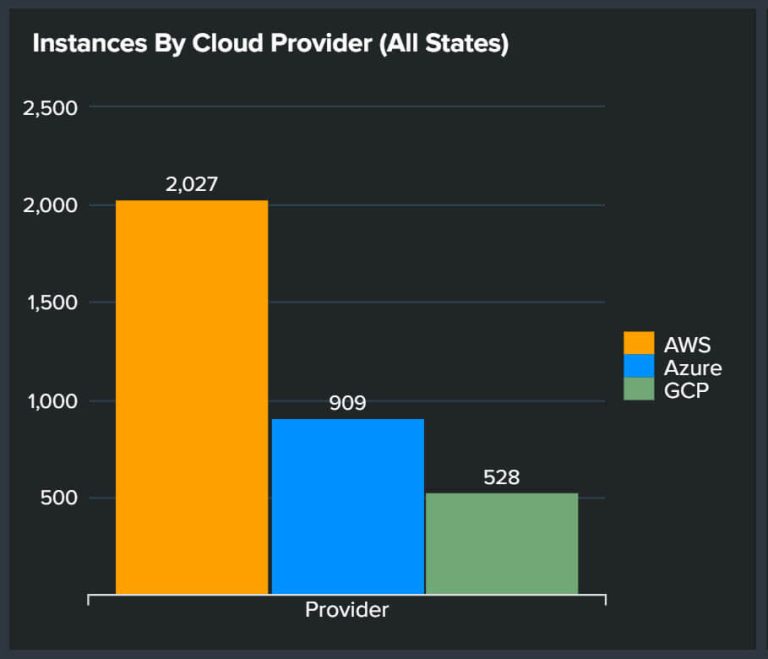
We offer security services across all cloud providers (AWS, GCP, Azure, DigitalOcean, Alibaba, IBM, Oracle, RedHat, Rackspace), hybrid environments, and on-site/collocation data centers.
We assign a dedicated team of security engineers, project and account managers based on your project’s length and complexity.
You can rely on us for both your day-to-day security operations needs and compliance management.
Yes! We offer emergency services. Please, connect with your account representative for more information.

In today’s digital landscape, robust cybersecurity infrastructure is an essential element of any business. The role of the Chief Information Security Officer (CISO) is pivotal

As a leading cybersecurity company, we provide a comprehensive suite of robust, state-of-the-art Vulnerability Assessment and Scanning services. Our specialty lies in proactively monitoring and

Modern web applications continue to be a challenge for organizations to secure as developers build increasingly complex business applications faster than ever. Many organizations are