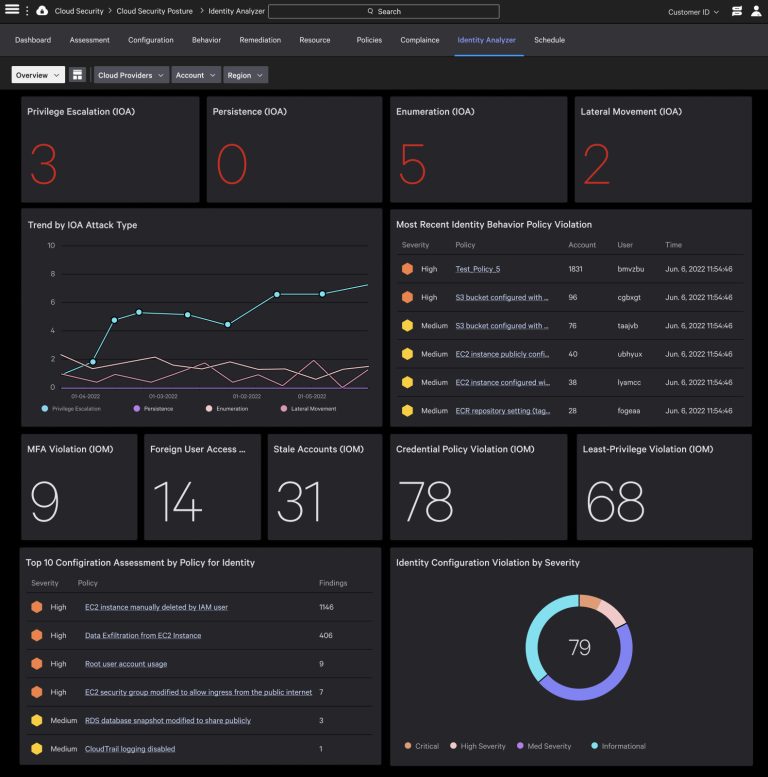
Continuous Security: Pen Testing, Asset Monitoring, and Effective Vulnerability Scanning
Protecting an organization today means staying ahead of changes that happen every hour – new code releases, spun-up cloud instances, employees joining from new laptops,