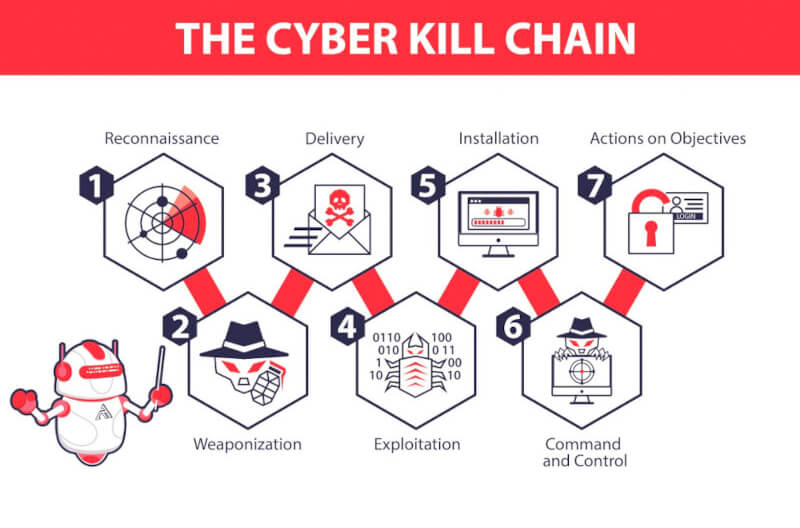
The cyber kill chain is an adaptation of the military’s kill chain, which is a step-by-step approach that identifies and stops enemy activity. Originally developed by Lockheed Martin in 2011, the cyber kill chain outlines the various stages of several common cyber attacks and, by extension, the points at which the information security team can prevent, detect or intercept attackers.
The cyber kill chain is intended to defend against sophisticated cyberattacks, also known as advanced persistent threats (APTs), wherein adversaries spend significant time surveilling and planning an attack. Most commonly these attacks involve a combination of malware, ransomware, Trojans, spoofing and social engineering techniques to carry out their plan.
There are several core stages in the cyber kill chain. They range from reconnaissance (often the first stage in a malware attack) to lateral movement (moving laterally throughout the network to get access to more data) to data exfiltration (getting the data out). All of your common attack vectors – whether phishing or brute force or the latest strain of malware – trigger activity on the cyber kill chain.
NOTE: There are couple of different implementation/versions of the cyber kill chain, we are covering here the one based on Lockheed Martin.
Each stage is related to a certain type of activity in a cyber attack, regardless of whether it’s an internal or external attack:
- Reconnaissance
The observation stage: attackers typically assess the situation from the outside-in, in order to identify both targets and tactics for the attack. - Intrusion
Based on what the attackers discovered in the reconnaissance phase, they’re able to get into your systems: often leveraging malware or security vulnerabilities. - Exploitation
The act of exploiting vulnerabilities, and delivering malicious code onto the system, in order to get a better foothold. - Privilege Escalation
Attackers often need more privileges on a system to get access to more data and permissions: for this, they need to escalate their privileges often to an Admin. - Lateral Movement
Once they’re in the system, attackers can move laterally to other systems and accounts in order to gain more leverage: whether that’s higher permissions, more data, or greater access to systems. - Obfuscation / Anti-forensics
In order to successfully pull off a cyberattack, attackers need to cover their tracks, and in this stage they often lay false trails, compromise data, and clear logs to confuse and/or slow down any forensics team. - Denial of Service
Disruption of normal access for users and systems, in order to stop the attack from being monitored, tracked, or blocked - Exfiltration
The extraction stage: getting data out of the compromised system.
Evolution of the Cyber Kill Chain
As noted above, the cyber kill chain continues to evolve as attackers change their techniques. Since the release of the cyber kill chain model in 2011, cybercriminals have become far more sophisticated in their techniques and more brazen in their activity.
While still a helpful tool, the cyberattack lifecycle is far less predictable and clear cut today than it was a decade ago. For example, it is not uncommon for cyber attackers to skip or combine steps, particularly in the first half of the lifecycle. This gives organizations less time and opportunity to discover and neutralize threats early in the lifecycle. In addition, the prevalence of the kill chain model may give cyberattackers some indication of how organizations are structuring their defense, which could inadvertently help them avoid detection at key points within the attack lifecycle.
Critiques and Concerns Related to the Cyber Kill Chain
While the cyber kill chain is a popular and common framework from which organizations can begin to develop a cybersecurity strategy, it contains several important and potentially devastating flaws.
Perimeter Security
One of the most common critiques of the cyber kill chain model is that is focuses on perimeter security and malware prevention. This is an especially pressing concern as organizations shift away from tradition on-prem networks in favor of the cloud.
Likewise, an acceleration of the remote work trend and a proliferation of personal devices, IoT technology and even advanced applications like robotic process automation (RPA) has exponentially increased the attack surface for many enterprise organizations. This means that cybercriminals have far more points of access to exploit—and companies will have a more difficult time securing each and every endpoint.
Attack Vulnerabilities
Another potential shortcoming of the kill chain is that it is limited in terms of the types of attacks that can be detected. For example, the original framework is not able to detect insider threats, which is among the most serious risks to an organization and one of the attack types that has the highest rates of success. Attacks that leverage compromised credentials by unauthorized parties also cannot be detected within the original kill chain framework.
Web-based attacks may also go undetected by the cyber kill chain framework. Examples of such attacks include Cross Site Scripting (XSS), SQL Injection, DoS/DDoS and some Zero Day Exploits. The massive 2017 Equifax breach, which occurred in part because of a compromised software patch, is a high-profile example of a web attack that went undetected due to insufficient security.
Finally, while the framework is intended to detect sophisticated, highly researched attacks, the cyber kill chain often misses those attackers who do not conduct significant reconnaissance. For example, those who use a “spray and pray” technique often avoid carefully laid detection snares by pure happenstance.
Role of the Cyber Kill Chain in Cybersecurity
Despite some shortcomings, the Cyber Kill Chain plays an important role in helping organizations define their cybersecurity strategy. As part of this model, organizations must adopt services and solutions that allow them to:
- Detect attackers within each stage of the threat lifecycle with threat intelligence techniques
- Prevent access from unauthorized users
- Stop sensitive data from being shared, saved, altered, ex-filtrated or encrypted by unauthorized users
- Respond to attacks in real-time
- Stop lateral movement of an attacker within the network
Alternatives:
In 2017, Paul Pols published the Unified Cyber Kill Chain to overcome and expand on the Cyber Kill Chain. The Unified Cyber Kill Chain was originally a university paper bringing together a number of Cyber Kill Chains by various industry contributors such as Laliberte, Nachreiner, Bryant, and Malone, but the real focus was on Lockheed Martin Cyber Kill Chain and MITRE ATT&CK. The Unified Kill Chain takes from all of these frameworks and proposed 3 high level steps attackers take:
- Initial Foothold
- Network Propagation
- Action on Objectives
More information available at: https://www.sans.org/blog/cyber-kill-chain-mitre-attack-purple-team/
MITRE ATT&CK Kill Chain model:
1. Recon
2. Weaponize
3. Deliver
4. Exploit
5. Control
6. Execute
7. Maintain