
Virtual CISOs: The Advantages of Hiring a vCISO
In today’s digital landscape, robust cybersecurity infrastructure is an essential element of any business. The role of the Chief Information Security Officer (CISO) is pivotal

In today’s digital landscape, robust cybersecurity infrastructure is an essential element of any business. The role of the Chief Information Security Officer (CISO) is pivotal

As a leading cybersecurity company, we provide a comprehensive suite of robust, state-of-the-art Vulnerability Assessment and Scanning services. Our specialty lies in proactively monitoring and

Modern web applications continue to be a challenge for organizations to secure as developers build increasingly complex business applications faster than ever. Many organizations are

In today’s interconnected digital landscape, ensuring the security of your organization’s systems and data is paramount. A crucial aspect of maintaining robust security is conducting

Threat Hunting is a creative process. One’s abilities to think abstractly, challenge ideas, and be unafraid of failure lead to more knowledge and breakthroughs than someone who does everything the same way every time.

The cyber kill chain is an adaptation of the military’s kill chain, which is a step-by-step approach that identifies and stops enemy activity.

As we navigate the complexities of the digital realm, ensuring robust security for businesses and individuals alike, we at Prodigy13 are acutely aware of another
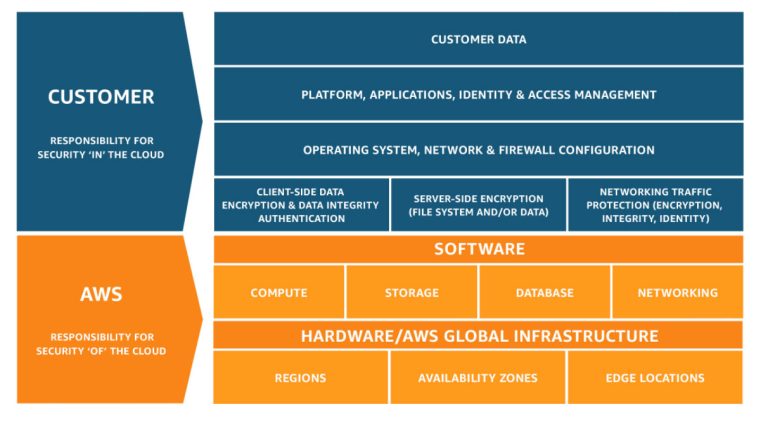
Security and Compliance is a shared responsibility between AWS and the customer. This shared model can help relieve the customer’s operational burden as AWS operates, manages and controls the components from the host operating system and virtualization layer down to the physical security of the facilities in which the service operates.

The Adversarial Tactics, Techniques, and Common Knowledge or MITRE ATT&CK is a guideline for classifying and describing cyberattacks and intrusions.
Get email alerts when we publish new blog articles!